Introduction
An ISE High Level Design (HLD) is recommended to assist you with the design and planning of your ISE deployment. Having a clearly written security policy – whether aspirational or active – is the first step in assessing, planning and deploying network access security. Without this, it is hard to break down the deployment into phases by location or capabilities. When seeking outside help, the HLD provides a huge time savings for education other teams, partners, Cisco Sales representative, Technical Assistance Center (TAC) representative or even the ISE product and engineering teams. Clearly state the desired solution capabilities, hardware and software environment and integrations can quickly allow people to understand what you want and how to configure it or troubleshoot it.
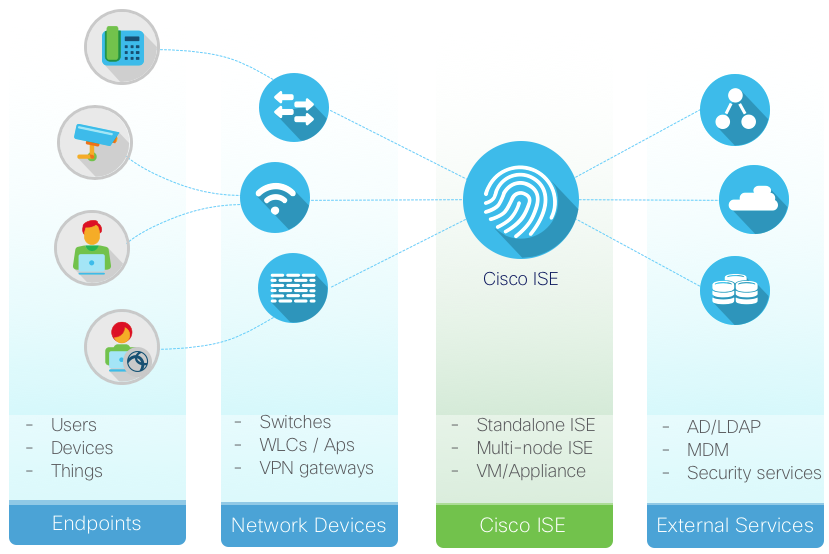
Business Objectives
Identify the Customer Business Objectives that ISE must solve. Typically this involves regulations and compliance or identified security threats and risks to smooth operation of the business or brand. But it also involves mitigating risks with controlled network access for everyday IT processes. This is how you begin to craft your network access control policy. The more specific you can be, the better.
Consider the following example business objectives that must translate into access control policy :
- We want to provide sponsored guest access to our visitors
- All network device administration commands must be authorized and logged for potential audit
- We want to identify all endpoints on our network so we can begin to apply access control policies
- We do not want our employees personal devices on our corporate network
- We want our employees to any device they want but we want to manage it to ensure it and any information on it is properly secured
- Printers should only talk to print servers
- We need to be able to re-image our workstations over the network via PXE
- We must comply with [PCI, HIPAA, etc.] regulation
- All Windows devices must be patched within the last 30 days to minimize known vulnerabilities
- We want to automatically quarantine endpoints when [Stealthwatch, AMP, etc.] detects malicious behavior
Business Objectives |
|---|
|
|
Environment
Physical Network Topology |
|---|
| <Insert image of your proposed ISE deployment here> |
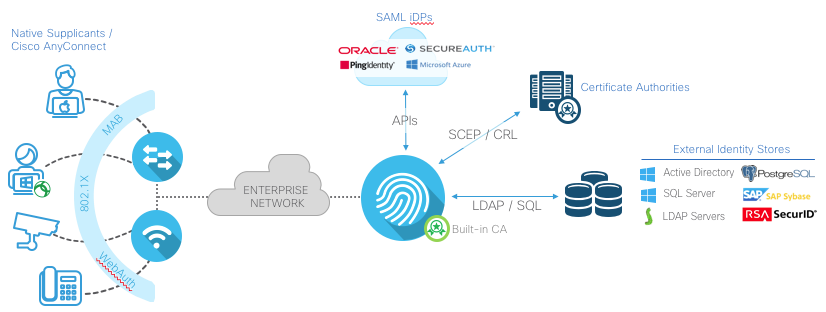
Identity Sources
List all of the products that ISE will need to integrate with or control. Please note any known issues or concerns with their behavior or capabilities.
Note: Cisco strongly recommends server certificate, which is signed by in-house CA or other 3rd party Root CA server, to be used for ISE. Self-signed server certificate should not be used for production deployment.
| Scenario (one line per device to be validated) | Vendor / Version | Count | Notes |
|---|---|---|---|
| Identity Sources | |||
Certificate Authorities (CA)
|
|||
Active Directory:
|
Microsoft | # | |
| LDAP | # | ||
| Token | # | ||
| SAML | # | ||
| ODBC | # | ||
| Social Login | Facebook? | # |
User Groups
Identify the specific user groups that will require differentiated access and for which scenarios.
| Scenario (one line per device to be validated) | Notes |
|---|---|
| Groups | |
Network Devices
Provide the general switch/controller model numbers/platforms deployed and Cisco IOS and AireOS Software versions to be deployed to support ISE design. Please use the ISE Compatibility Guides to see our latest list of Validated products and protocols. If you still don’t believe that ISE supports heterogeneous networks and can support your network devices, please read Does ISE Support My Network Access Device?
| Vendor | Hardware Model
@ Software Version |
Count | Notes |
|---|---|---|---|
| Wired | |||
| Cisco | 9300 @ 15.x.x | # | |
| Wireless | |||
| Cisco | WLC xxxx @ 8.x | # | |
| Cisco | Meraki xxxx | ||
| Aruba | @ 7.x | ||
| VPN | |||
| Cisco | ASA 55xx @ x.x | # |
Endpoints
List all of the unique endpoint types you expect to find and apply policy to in your deployment.
Provide an approximate number of each of possible.
Note: For domain joined Windows machines to function properly, machine authentication is recommended. Performing user only authentication may break critical functions such as machine GPO and other background services such as backup and software push.
Note: State whether the deployment is using machine or user authentication, or both. If both machine and user authentication are planned, are Machine Access Restrictions (MAR) planned? If so, review the Appendix information on MAR caveats. For machine / user authentication details, please refer to 802.1X Authenticated Wired and Wireless Access
| Endpoints (one line per endpoint to be validated) | Vendor | Hardware Model
@ Software Version |
Estimated Count |
Notes |
|---|---|---|---|---|
| Workstations | ||||
| Microsoft | Windows XP | # | ||
| Microsoft | Windows 7.x | # | ||
| Microsoft | Windows 8.x | # | ||
| Microsoft | Windows 10 | # | ||
| Microsoft | Windows Embedded | # | ||
| Apple | MacOS 10.13 | # | ||
| Chromebook | ||||
| Linux | Linux | # | ||
| VDI | ||||
| Mobile Devices | ||||
| Apple | iOS 11.x | |||
| Android | Android 8.x | |||
| Android | Android 7.x | |||
| Android | Android 6.x | |||
| Office | ||||
| Access Points | Cisco | # | ||
| IP Phones | Cisco | 7xxx | # | |
| Printers | # | |||
| IOT | ||||
| Cameras | # | |||
| Lighting | # | |||
| Badging | # | |||
| HVAC | # | |||
| Medical | # | |||
| Manufacturing | # | |||
| SCADA | # | |||
| Others | # | |||
| Approximate Total: | ### |
ISE Cube
List all of the nodes in your ISE deployment.
When deploying VMs:
- The VM host should be sized comparably with the ISE hardware appliance(s)
- The resources need to be reserved for each ISE node and cannot be shared among different ISE nodes or other guest VMs on the host.
- Hard disks with 10K or higher RPM are required. Average IO Write performance for the disk should be higher than 300MB/sec and IO Write performance should be higher than 50MB/sec. Please make sure to reserve the RAM and CPU cycles for the ISE node deployed as VM.
- If disk size needs to be resized, the node will need to be re-imaged from the ISO
| Host Name (FQDN) | Persona | IP Address | VM/HW | Size | Storage |
|---|---|---|---|---|---|
| ise1.cordero.me | PAN+MnT | VM | 3595 | 600GB | |
Device Administration (TACACS+)
Differentiated access for network device administrators
| Scenarios | ✓ Done | Notes |
|---|---|---|
| SuperAdmin | ||
| Script | ||
| Read-Only Admin |
Visibility
See what, when, where and how users and endpoints are on your network.
In the table below, list the primary endpoint devices (one per row) that need to be profiled.
- Identify the primary device types to be profiled
- Which probes/protocols will be used to collect the required data? Leverage Device Sensor to collect endpoint attributes whenever possible and SNMP for other network devices. Uncommon devices may require collecting additional protocol attributes to classify the endpoint properly.
- ISE Probes: AD, DHCP, DNS, HTTP, NMAP, RADIUS, SNMP, Netflow
- Device Sensor: CDP, LLDP, DHCP, HTTP, H323, SIP, MDNS
- AnyConnect: ACIDex
- What is the endpoint attribute data required to classify each device type?
- Is profiling for visibility only or for use in authorization policy?
- Leverage Device Sensor to collect endpoint attributes whenever possible and SNMP for other network devices
- Uncommon devices may require collecting additional protocol attributes to classify the endpoint properly.
- For Visibility with SPAN/RSPAN, use a dedicated interface on the ISE PSN for the DHCP SPAN or HTTP SPAN probe.
- If RSPAN or Netflow is to be used:
- does infrastructure support these technologies?
- a dedicated interface should be used on the Policy Service Node for the DHCP SPAN or HTTP SPAN probe. Is there sufficient bandwidth between source SPAN/Netflow exporter and ISE Policy Service node used for profiling?
| Scenarios | ✓ Done | Notes |
|---|---|---|
| Enable Profiling Feed Service or retrieve offline update | ||
| Create Custom Endpoint Profiles for _____ Devices | ||
| Create Endpoint Purge Policies | ||
| Move profiled endpoints to static MAC-based endpoint lists and do not use endpoint profiles in authorization rules if you want to minimize Plus License consumption |
||
Secure Access
Control authenticated endpoint & user access
| Scenarios | ✓ Done | Notes |
|---|---|---|
Wireless |
||
| Wireless 802.1X User Authentication & Authorization: Show Successful Login and Role-Based Access | ||
| Wireless Machine Authentication and Authorization: use digital certificate for Corporate device | ||
| Individual Pre-Shared Key (iPSK) | ||
| Static Endpoint MAC Whitelisting: allow non-authenticating (no 802.1X) endpoints with MAB | ||
| Wireless user with Passive Identity (No 802.1x) | ||
| eduroam | ||
Wired |
||
| ISE Wired Access Deployment Guide | ||
| Static Endpoint MAC Whitelisting: allow non-authenticating (no 802.1X) endpoints with MAB | ||
| Static Endpoint MAC Blacklisting: block non-authenticating endpoints with MAB | ||
| Dynamic Endpoint Profiling and Authorization: List each endpoint profile and the desired authorization | ||
| Easy Connect: Wired user with Passive Identity (No 802.1X supplicant) | ||
| Wired Web Authentication (No 802.1X Supplicant. For Guest or Employees) | ||
| EAP-Chaining: Wired machine+user authentication using EAP-FAST with AnyConnect | ||
| Wired Machine Authentication and Authorization: use digital certificate for Corporate device | ||
| Wired User 802.1X Authentication: Show Successful Login and Role-Based Access | ||
| Wired WebAuth Login: Show Login With No Supplicant | ||
| Wired Authentication (user or machine) & Authorization on a Docking Station | ||
| Wired Authentication for a user via an Windows Remote Desktop Protocol (RDP) Session | ||
| Wired Authentication for Multi-User devices (Nurses Station, Call Center, etc.) | ||
| Wired Authentication (user or machine) & Authorization on a Docking Station Behind IP-Phone | ||
| Wired Authentication with Two-Factor Authentication (2FA) | ||
VPN |
||
| VPN Authentication and Authorization with Username:Password: Show Successful Login and Role-Based Access | ||
| VPN Authentication and Authorization with Token/2FA: Show Successful Login and Role-Based Access | ||
| VPN Access Attempt, Revoked Certificate (Testing OCSP) |
Guest
Internet access for visitors. Generally, you should only implement one type of Guest network.
| Scenarios | ✓ Done | Notes |
|---|---|---|
HotSpot |
||
Customize Portal
|
||
| Demonstrate Hotspot with desired flow: | ||
Self-Registered |
||
| Create desired Guest Types | ||
| Demonstrate Self-Service Guest registration | ||
Sponsored |
||
| Customize Sponsor Portal Flow and Presentation | ||
| Create Sponsor Groups | ||
| Demonstrate Sponsor Portal (sponsored Guest access) | ||
| Login with Sponsored Guest Credentials | ||
| Concurrent Guest Logins | ||
API |
||
| Guest API integration with external application(s) |
BYOD
Onboard & differentiate personal & corporate devices. Consider the following topics when determining your scenarios:
- Is it Single SSID or Dual SSID?
- Will Android be in the BYOD design? If so, please provide details of provisioning authorization profile
- What devices will and will not be provisioned?
- What supplicant will be used? Native or AnyConnect or Other?
- What access will unsupported device get? (i.e. Blackberry, Windows phones, Chromebooks)
- Will EMM/MDM be integrated with BYOD design? If so, please provide details of MDM policy below in the Authorization Policy section and whether or not redirection will be used for MDM agent installation
| Scenarios | ✓ Done | Notes |
|---|---|---|
| Device Registration | ||
| Single SSID: Unregistered devices are redirected to a WebAuth portal and respective users | ||
| Dual SSID: Unregistered devices are redirected to a WebAuth portal and respective users | ||
| Certificate Provisioning | ||
| BYOD: Onboarding, Certificate Provisioning with Internal or External CA | ||
| Certificate Expiration with Internal or External CA | ||
| Certificate Renewal 2-4 weeks before Certificate Expiration | ||
| Device Management | ||
| Certificate Revocation by Administrator | ||
| End-User self management, Device Lost; Blacklist endpoint | ||
| End-User self management, Device Stolen; revoke Certificate |
Integrations
Share contextual information with other products
| Scenarios | ✓ Done | Notes |
|---|---|---|
Context Sharing |
||
| Demonstrate pxGrid integration with SIEM | ||
| Share identity context with StealthWatch via pxGrid | ||
| Cisco Industrial Network Director shares IOTAsset topic with ISE | ||
| ISE brokers pxGrid topic sharing among partners | ||
| … | ||
Threat Mitigation |
||
| Rapid Threat Containment (RTC) | ||
| Threat-Centric NAC Integration with Vulnerability Scanner or AMP | ||
| … | ||
APIs |
||
| Integrate Guest Management workflow from another application | ||
| Integrate DNA Center with ISE for Access Control Policy and software-defined Segmentation with TrustSec | ||
| Integrate network management tool for adding/updating/removing network devices, endpoints, etc. | ||
| … |
Compliance
Ensure that endpoints meet security standards.
Review the list of currently supported packages for Windows and MacOSX.
| Scenarios | ✓ Done | Notes |
|---|---|---|
| Agent-less | ||
| Posture Windows with Temporal Agent | ||
| Posture MacOS with Temporal Agent | ||
| Agent-ed | ||
| Non-Compliant endpoints are quarantined and redirected to provision AnyConnect and the Posture Module via ISE | ||
| Non-Compliant endpoints are quarantined and redirected until provisioned by [WSUS, etc.] | ||
| Compliant endpoints are properly authorized on the network | ||
| Enterprise Mobility Management (EMM) / Mobile Device Management (MDM) |
||
| Integrate ISE with EMM/MDM vendor(s) | ||
| Non-Compliant endpoints are quarantined and redirected until provisioned by [WSUS, etc.] | ||
| Compliant endpoints are properly authorized on the network |
Posture Policies
Describe posture policy requirements for endpoint compliance. This may include many areas such as asset checking, application and services checking, and antivirus and antispyware checks, as well as customized checks for specific use cases. Describe remediation plans and include remediation servers that need to be integrated into the design.
| Rule Name | OS (Windows/MacOSX) | Conditions | Posture Agent | Checks | Remediation | Enforcement (Audit/Opt/ Mandatory) |
When Assessed (Login/PRA/Both) |
|---|---|---|---|---|---|---|---|
| Employee_AV | Windows XP/7 | AD group= Employee | NAC Agent for Windows | AV Rule: Microsoft Security Essentials 2.x |
Live update (Automatic) | Mandatory | Both |
| Employee_Asset | Windows XP/7 | AD group= Employee | NAC Agent for Windows | Custom registry check | Link redirect to policy page (Manual) |
Mandatory | Login |
| Contractor_AV | Windows ALL | ID Group= Contractor | Web Agent | AV_Rule: Any AV w/current signatures |
Local Message regarding AV Policy | Mandatory | Login |
Client Provisioning Policies
Describe Client Provisioning policy requirements for posture and native supplicant provisioning.
| Rule Name | Identity Groups | Operating Systems | Other Conditions | Results |
|---|---|---|---|---|
| Apple | Any | MAC OSX or Apple iOS | Native Supplicant:EAP-TLS, SSID | |
| Windows | Any | Windows All | Agent: NAC AgentNative Supplicant:PEAP-MSCHAPv2, SSID |
|
| Android | Any | Android | Native Supplicant:EAP-TLS, SSID |
Segmentation
Limit exposure with pre-defined access segmentation
| Scenarios | ✓ Done | Notes |
|---|---|---|
| Classification | ||
| Dynamically classify endpoints with SGTs via MAB (static or profiled, e.g. IOT) | ||
| Dynamically classify endpoints with SGTs via 802.1X Machine Authentication | ||
| Dynamically classify users with SGTs via 802.1X Authentication | ||
| Dynamically classify users with SGTs via Easy Connect (MAB+Passive Identity) | ||
| Dynamically classify users with SGTs using WebAuth (e.g. Guests) | ||
| Statically classify traffic by VLAN | ||
| Statically classify traffic by Subnet | ||
| Statically classify traffic by L2 Interface | ||
| Statically classify traffic by L3 Port | ||
| Statically classify traffic by VM (port profile) | ||
| East-West Segmentation | ||
| Malware blocking between Employees | ||
| Virtual machines in the data center | ||
| Firewall Rule Reduction | ||
| Use group-based policies to reduce firewall rules by eliminating need to specify IPv4/IPv6 addresses | ||
| User to Data Center | ||
| Use group-based policy to enforce access to resources in the data center |
Containment
Reduce risk with rapid threat containment.
| Scenarios | ✓ Done | Notes |
|---|---|---|
| Scenario 1 | ||
| Scenario 2 | ||
| Scenario 3 |
Operations & Management
List the day-to-day operations you anticipate needing to do.
| Scenarios | ✓ Done | Notes |
|---|---|---|
| Monitoring | ||
| Real-Time Event Log (Live Log) | ||
| Illustrate the Live Log Authentication Details | ||
| Debug Endpoint (Working across entire ISE deployment) | ||
| TCP Dump from Central Location | ||
| Troubleshooting Active Directory – Basic and Detailed | ||
| Policy Export | ||
| Suppression Bypass | ||
| Collection Filters | ||
| NAD Syslog Correlation in Reports | ||
| Time-Range Bound Support Bundles | ||
| Guest Activity Monitoring | ||
| Management | ||
| Create a Wildcard Certificate for an ISE deployment | ||
| Centralized, Encrypted Backup | ||
| Create and run Scheduled or On-Demand Backups | ||
| RBAC, with predefined roles, customize, add and remove options, Help desk accounts, super user account. | ||
| Centralized Monitoring of All ISE Nodes | ||
| Simultaneous Admin Users Logged in & working with ISE | ||
| Enable and use External RESTful Services (ERS) APIs | ||
| Demonstrate the Upgrading of ISE Nodes with Zero Down Time |
Scale & High Availability
List the scale and HA scenarios you want to test.
| Scenarios | ✓ Done | Notes |
|---|---|---|
| ISE Cube | ||
| Multi-Forest AD Join | ||
| Multi-AD within Single Forest Joins | ||
| Policy Admin Node (PAN) Down | ||
| Policy Service Node (PSN) Down | ||
| Survivability & High Availability | ||
| Identity Store (AD) Down/Unavailable | ||
| Remote Site WAN Link Down | ||
| Reinitialization once WAN is back up | ||
| Fail Open | ||
| Fail Half-Open (Critical ACL) | ||
| Fail Closed | ||
Policy Details
List all security policies that are needed to implement the business requirements described above.
Authentication Policy
For each use case (wired, wireless, VPN), describe the authentication policies that will be implemented for all users and endpoints whether managed or unmanaged.
| Rule Name | Condition | Allowed Protocols | ID Store / ID Sequence |
|---|---|---|---|
| Device Access | Wired_MAB | Default Network Access | Internal EndPoints |
| 802.1X Access | Wired_802.1X | Default Network Access | AD_then_Local |
| VPN | NAS-Port-Type = Virtual | Default Network Access | AD |
| Default | – | Default Network Access | Internal Users |
Authorization Policy
For each use case (wired, wireless, VPN), describe the authorization policies that will be implemented for all users and endpoints whether managed or unmanaged.
| Rule Name | Identity Groups | Other Conditions | Permissions |
|---|---|---|---|
| BYOD Unknown | Mobile Devices Logical Group | EAP Tunnel = PEAPEAP Type = MSCHAPv2 | NSP dACLNSP Redirect |
| BYOD Registered | Registered | EAP Type = EAP-TLSSAN = Calling-StationID | Registered dACL |
| IP_Phones | Cisco-IP-Phones | – | Voice VLAN Authz VVID |
| Printers | Managed-Printers | – | Printer VLAN |
| Cameras | Managed-Cameras | – | Camera VLAN |
| Workstation_Access | Any | Domain PC | AD Access dACL |
| User_Role_1_Access | Any | Domain Member Role1 | Role1 dACL |
| User_Role_2_Access | Any | Domain Member Role2 | Role2 dACL |
| Guest_Access | Guest | – | Internet Only dACL |
| Default | – | – | Web Auth |
Source:
https://community.cisco.com/t5/tkb/articleprintpage/tkb-id/4561-docs-security/article-id/5824